Category: Articles
-

BlackLotus: Microsoft will repair recent Secure Boot vulnerability
Microsoft provided a patch earlier this week to remedy a Secure Boot bypass problem utilised by the BlackLotus bootkit. The first vulnerability, CVE-2022-21894, was patched in January. However, the current patch for CVE-2023-24932 addresses another commonly exploited workaround for computers running Windows 10 and 11. Also on Windows Server versions dating back to Windows Server…
-

WordPress Plugin: A Critical Vulnerability Discovered
Over one million WordPress websites are now vulnerable to attacks. This aims to give unauthorised access to user accounts with elevated privileges. The flaw is due to a newly identified vulnerability in the Essential Addons for Elementor plugin. A cyber security website researcher highlighted the new vulnerability (CVE-2023-32243) in an alert released on Thursday. New…
-

Man in the middle in phishing attacks are increasing
Man-in-the-middle attacks used in phishing are becoming more and more common. Because man-in-the-middle assaults in phishing operations are so effective, criminals are increasingly using them. According to a report from cybersecurity website, hackers are enticing victims to web servers capable of brokering the full authentication process rather than just one phoney login page where they…
-

WordPress plugin vulnerability affected more than 2 million sites
Following a security issue, users of the Advanced Custom Fields WordPress plugins are being recommended to update to version 6.1.6. The security flaw, known as CVE-2023-30777 is reflected in cross-site scripting (XSS). Moreover, it may be exploited to insert arbitrary executable programmes into otherwise secure web pages. There are more than two million active installs…
-

Gmail is mixing ads with ordinary emails
Do you like the ads in your Gmail account? No? Unfortunately, it appears that we will receive much more, which is unfortunate. Several internet screenshots demonstrate how users of Gmail for desktop and mobile are seeing far more advertisements than normal. Gmail has always included ads. However, they are often hidden at the top of…
-

Threats to cloud security are expanding more quickly
Cloud security dangers are expanding more quickly than ever. As threat actors discover fresh and inventive ways to spread malware using cutting-edge technologies, More than half (55%) of all HTTP and HTTPS malware downloads originated via cloud apps, according to Netskope’s most recent Cloud & Threat Report: Global Cloud and Web Malware Trends study,…
-
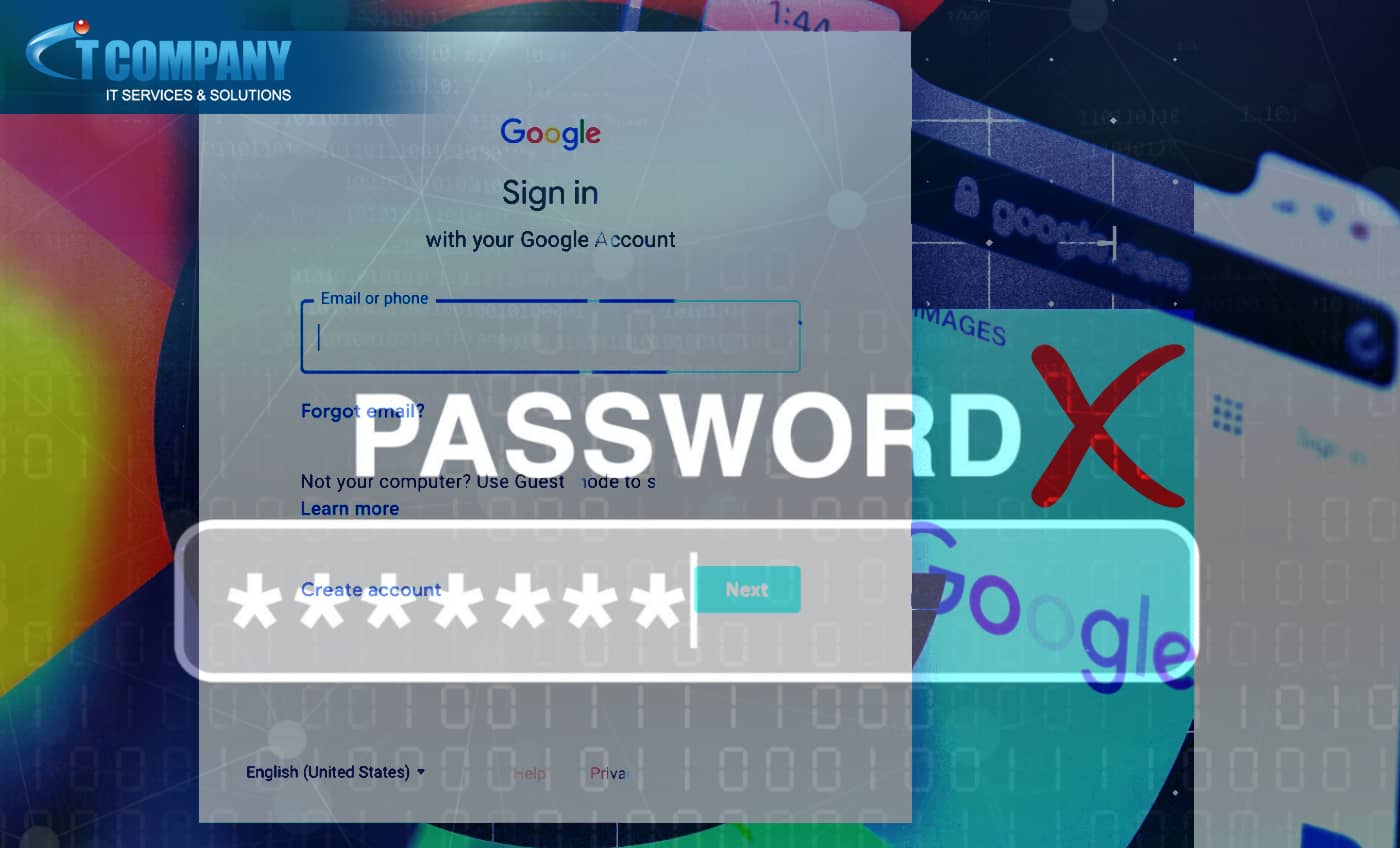
With passkey Google allows you to sign in without passwords
Passkeys enable you to access your Google account only using biometrics. We all despise passwords: generating, remembering, storing, and using them. Google has now made a significant step towards a password-free future, relying instead on passkeys. With a passkey, you can now access your Google accounts without using a password by scanning your face or…
-

Protect Web Applications from AI-Assisted Cyber Attacks
In this blog, we’ll look at how AI is changing the threat environment, emphasising the rising AI-powered cyber assaults. We will talk about how organisations may strengthen their security posture by embracing technology and using practises to combat attacks. AI has ushered in a new era of innovation. As its revolutionary influence is being…
-

To steal credit cards, hackers are using genuine checkout forms
Hackers are stealing credit cards from unwary customers by hijacking internet retailers and displaying sophisticated, realistic-looking bogus payment forms. These payment forms are displayed as modal, HTML content that is overlaid on top of the main webpage. Moreover, it allows the user to interact with login forms or notification material without leaving the page. When…
-

New Gmail scam: here’s how to keep your inbox safe
Google Rewards are being used as bait in a new Gmail scam. A horrible new Gmail scam is circulating, with some users reporting receiving emails with the subject line “Online Reward Program”. However, like with other unwanted emails, it’s too good to be true. Despite claiming to be from Google Workspace company and that the receiver…